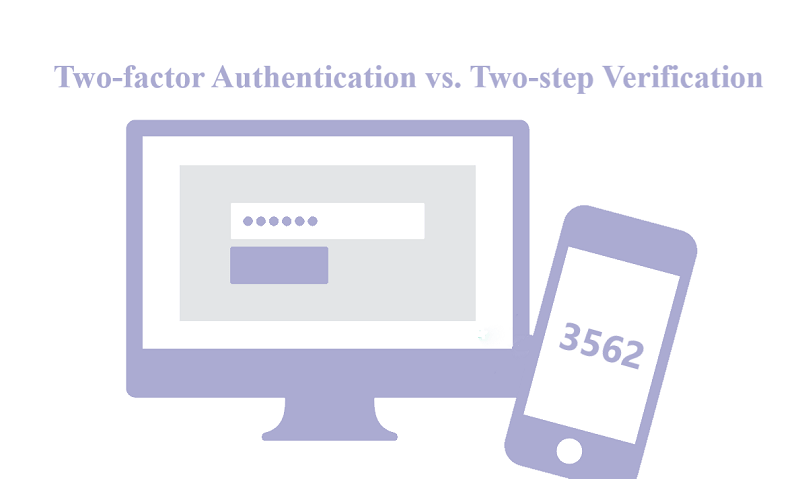
First of all, you should bear in mind that two-factor authentication is not two-step verification. Although they are security methods for your Apple ID that work in a similar way, there are noticeable differences between them in many aspects.
What is two-step verification?
According to Apple, “Two-step verification is a security feature for Apple ID that’s designed to prevent anyone else from controversy or using your account, even if they know your password.”
In other words, you can only log into the account after entering the verification code. For example, when you sign into a web service for which you enabled this feature, you need to fill in the verification code you receive to verify your identity. This is what we call two-step verification.
What is two-factor authentication?
According to Apple, “Two-factor authentication is an extra layer of security for your Apple ID designed to ensure that you’re the only person who can access your account, even if someone knows your password.”
Apple’s two-factor authentication is similar to its two-step authentication. But it doesn’t send verification code via messages. When you log in to your Apple ID in a new location or on a new device, you will get an alert about this login on your trusted device and a six-digit verification code will also be generated. You have to enter the verification code before proceeding to the next step.
The differences between two-step verification and two-factor authentication
- How to enable them?
To turn on two-step verification, you need to go to your Apple ID account page. While two-factor authentication is only available when you are using iOS 9 or later or OS X El Capitan or later. You should enable it on an iOS or macOS device on which you have logged in with your Apple ID.
- Trusted devices
When enabling two-step verification, you will be required to send a verification code a device that uses Find My iPhone or SMS to register a trusted device.
While all devices that have signed in to iCloud will be automatically set as trusted devices if you turn on two-factor authentication for your Apple ID.
Both methods require you to verify a trusted phone number manually.
- Recovery key
Two-step verification generates a 14-character recovery key for you to regain access to your Apple ID in case you forget your password or lose the trusted devices.
You won’t get a recovery key from two-factor authentication.
- How do they work?
When logging into your Apple ID on an untrusted device or browser, both security methods will request an additional verification code to verify your identity.
After entering your Apple ID account and password, you will be asked to select a trusted device or phone number to receive a 4-digit verification code if you use two-step verification.
If you use two-factor authentication, you will get login alerts on all your trusted devices. And you can also choose a trusted phone number to receive the verification code.
Unlike two-step verification, the verification code will be extended from 4 digits to 6 digits and the login alert will show you the approximate location of this untrusted device. Besides, you can choose whether to allow the login attempt on any new devices. When you click on “Allow”, a 6-digit verification code will be automatically displayed on the device. If someone else is trying to sign in to your Apple ID on other devices, you can tap “Don’t Allow” to reject the login attempt. Once you make a choice on one device, the login alerts on other trusted devices will automatically disappear.
- Devices to receive verification code
The verification code for two-step verification can only be sent to iOS devices. While two-factor authentication allows users to send a verification code to iOS devices as well as Macs.
- Offline usage
Two-step verification doesn’t work when all trusted devices and phone numbers are offline. So, you may get into trouble with your login.
Fortunately, you can still get a verification code for two-factor authentication even if your trusted devices are offline, which greatly optimizes the user experience.
If you want to log into your Apple ID on a device that runs an older version, you need to get a verification code on a trusted device that uses iOS 9 or later or OS X El Capitan or later. Then, add the 6-digit verification code to the Apple ID password that is entered in the password field of your old device.
- Change security information
With two-step verification enabled, you can only change security information such as trusted devices on your Apple ID account page.
Two-factor authentication allows you to adjust security settings on your device.
- What if you forget your password?
To access your Apple ID, two-step verification requires that you have any two of the three things – password, recovery key and a trusted device. Otherwise, you could permanently lose access to your Apple ID.
Since two-factor authentication doesn’t give you a recovery key, you can’t regain access to your Apple ID with a recovery key. But you can use account recovery to get your Apple ID back. To get it back as quickly as possible, you need to provide detailed account information.
- Can I turn them off?
You can turn off two-step verification on your Apple ID account page. While two-factor authentication can on longer be turned off once you turn it on.
- You can’t use them together
Two-step verification is an old security method available for both Apple users and other users. If you have upgraded your device and want to use two-factor authentication, you need to turn off two-step verification first. By default, two-step verification will be automatically upgraded to two-factor authentication when you upgrade to iOS 11 or later, or macOS High Sierra or later.
Conclusion
It’s a good idea to secure your Apple ID with two-step verification or two-factor authentication. If you are looking for a reputable VPN to secure your Internet connection, we recommend you use RitaVPN.