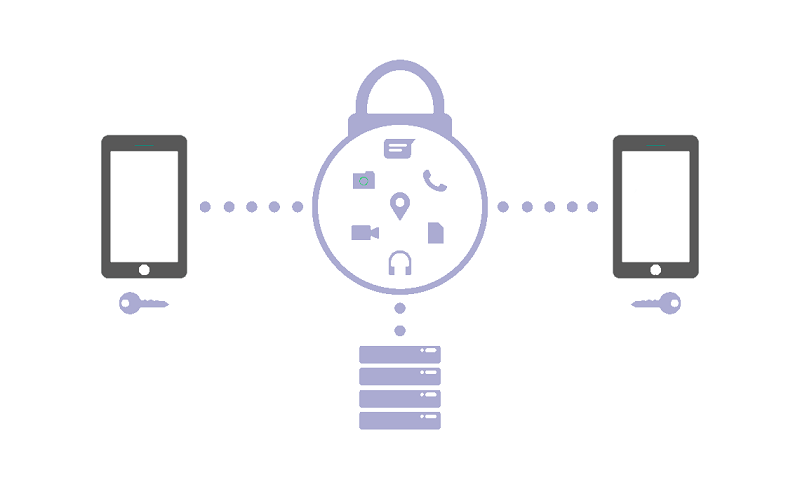
End-to-end encryption is by far the most reliable way for secure and private online communication. End-to-end communication does not allow others to read or access the private conversation, and this is accomplished by encrypting the messages of both the users. Recent advancements in the technology have made end-to-end encryption accessible and straightforward.
What is Encryption?
Encryption is the encoding of messages which can be only decrypted or decoded by the receiver of that message. Encryption software transforms the messages into some pattern called ciphertext that is unintelligible. It is developed as a secure way of communication that keeps the audience away from that conversation.
If someone accessed your messages, they would not be able to decode these messages without the key. It is not possible to break the high-level encryption because a 256-bit key is used to create a combination of 2 ^ 256. No supercomputer can break a key in a reasonable period.
That’s how encryption works;
- A directly readable text (“Hello Dad”) is encoded into an incomprehensible, garbled message (“OhsieW5ge+osh1aehah6”).
- This encrypted text is sent through the Internet, where the others get only the garbled text “OhsieW5ge+osh1aehah6.”
- When that message is received at the recipient side, only the intended recipient can decode or decrypt the message into the original message(“Hello Dad”)
- The recipient and only the recipient does have some way to decrypt it back into the original message when it arrives at its destination (“hello mum”).
What is End-to-End Encryption (E2EE)
This method is different and much better than simple encryption techniques that most of the companies are using. These companies have the encryption keys of your messages, and they can access them. For example, Hotmail and Gmail can read your mails.
End-to-end encryption (E2EE) encodes or encrypts your texts among the two end-points across the entire journey. When transiting through the servers, the messages remain encrypted, and no one can access these messages, including your ISP provider, service provider, or some third party.
What are the types of encryption?
Two types of encryption are Symmetric Encryption and Asymmetric Encryption.
What is Symmetric Encryption
When both the receiver and the sender use the same personal encryption key for decoding and encoding an encrypted message, it is called Symmetric encryption. The drawback of symmetric encryption is the sharing of the key between the two parties.
A secure and protected tunnel needs to be established so that no interceptor can grab the key for decoding the message.
Asymmetric Encryption
Asymmetric encryption is using a more secure and latest way to provide you more security. It encrypts your message by two keys, a private key and public key. Both the receiver and sender use the same public key but they both use a different private key. The sender and the receiver of the messages do not know the private key of each other. Both the keys are required to access the message.
What are the Advantages of End-To-End Encryption
There are many advantages of using the end to end encryption for communication.
Secures your Data: End to encryption ensures that only a few people can read your messages. In some case, I the hackers attack your server, and they steal all of your information. But they won’t be able to read your encrypted messages because only you have the decryption keys.
Keeps the Data Private: Google has complete access to your emails. Google can also save those emails which you have deleted from your side. By using end to end encryption, you can easily control who can read and access your messages.
Perfect for Democracy: Everybody is entitled to privacy. End to end protection protects the freedom of expression and protects against intimidation, oppressed dissidents, activists, and reporters.
How to use End-to-End Encryption
You can implement end-to-end encryption on your own, but this is a very complex task. Ensure that you have this feature in the service or software you are using, and you need to enable it to communicate safely. If you manage confidential information such as financial data or personal information, you must use it.
- End to end encryption secures instant messaging applications. Many applications like Messenger and Telegram do not have enabled this fantastic feature by default. So you should allow this feature to secure your messages.
- E2E also secures mailing communication. Secure your mails, and only the intended recipient can read the message.
- E2E encryption is often called the client-side encryption in P2P service and backup. It only encodes your information until it arrives at the service provider. In this case, zero-knowledge encryption is much better because it encodes your data, which can only be decrypted with your device or account.
- Your service provider cannot access your data, but if somehow you lost your device or forgot the password so you will lose all of your data.
Risks of using End-to-End Encryption
- Endpoints are not protected while using E2E, and if some hacker hacks any of your devices, he can access the private and public keys. Hackers can also steal your personal information through your application.
- Most applications provide you the backup of your data. This data is not encrypted and can be accessed by intruders. Always ensure to implement the E2E encryption on all the applications.
- Backdoor assault is a secret encryption bypass. Using the malware, trojans, or malicious code, hackers can make backdoor attacks. Hackers could intercept your computer and access your personal information.
Virtual Private Network
You should use a VPN service to protect yourself against the online packet sniffer and cybercriminals. RitaVPN is one of the most secure and best VPN services that encrypt all of your data, and no one can monitor your activities. It changes your IP address, and you can access the blocked websites or content. Download the RitaVPN from the official website and stay safe from all the hackers and cybercriminals.