Reading this article typically implies that you must have heard about transparent proxies. Internet service providers the world over, actually use these transparent proxies discreetly to be able to monitor the internet connection of users. It is difficult for the casual internet user to notice transparent proxies when they are used, and moreover, it is harder to avoid them. The only way that this is possible is through the use of a VPN. In this piece of editorial, you shall be thought about why the transparent proxies should concern you as well as how to bypass the system.
What transparent proxies mean?
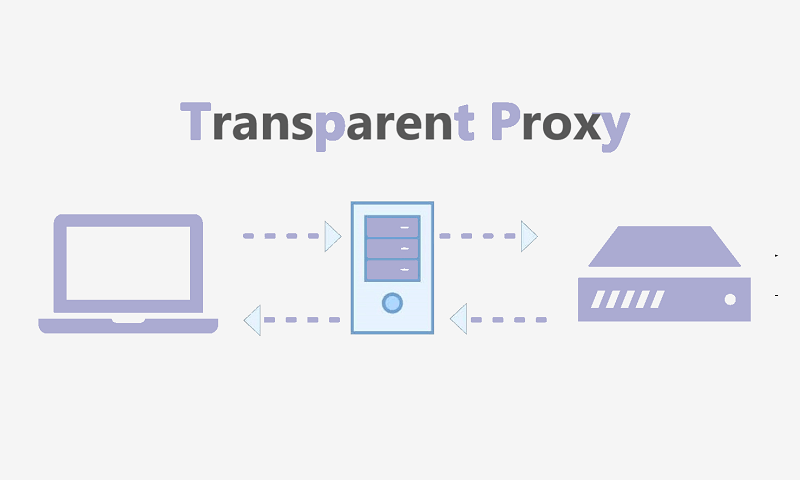
Typically, transparent proxies are known as servers which filter, redirect in addition to caching your traffic in a way that you cannot detect. Naturally, these transparent proxies are not harmful. Numerous business entities make use of transparent proxies as a means of protection against potential attacks (especially attacks from DDoS).
But, if the ISP which you are having uses this transparent proxy, you should be worried. The thing is, apart from the fact that it will be hidden by your ISP from you, it could also be used to track your traffic, used for data logging, as well as been used to scrutinize your activities online. This is to say that the transparent proxy typically provides information to your ISP about all the things that you do online.
Actually, by now, everyone has used to the fact that most governments of different countries monitor and track their communication. However, only a few people know that they still have to watch their Internet service provider. The scary truth is the fact that as this transparent proxy is quite common around the Middle East plus Asia, ISPs that are based in Canada, US plus the EU, make use of them more frequently than most people tend to think.
How can transparent proxies be detected?
Finding out to see if the USP you are using makes use of the transparent proxy. But, you can always make use of a simple checker for a proxy, such as the handy tool from whatismyip.network. Which can typically indicate whether you are being monitored by the transparent proxies or if you are not?
There exist other tech-savvy methods that can be used to detect these transparent proxies. However, this is not a subject that is suitable for now because of the sophisticated IT knowledge it needs. Overall, if the tool mentioned is used, you are either going to get just a single one out of three possible answers. No, you have no proxy; sure, there exists a proxy as well as there possibly exists a proxy. To be safe, just think about the probably as a sort of yes and do the right thing.
Find out if you are being monitored by the transparent proxy
An easy way to see if you are being tracked with the transparent proxy typically is trying to link to a certain server which you are aware is not in existence. If there isn’t any proxy, naturally, you will get an error message on your browser. The Chrome browser usually says, “The website cannot be accessed,” because the IP address of the website cannot be discovered.
If there is a proxy that is tracking your online activities, this error message could appear differently, or you could be rerouted to a different page like a search engine page.
If you don’t get a direct result from that, several websites have services that detect transparent proxies with various levels of efficiencies.
If you log on to a website that is encrypted with HTTPS, if you click the lock symbol, you will be provided with several fundamental information relating to the SSL certificate of the website. If your ISP had been issued this certificate rather than the owner of the website, this could be an indicator that you are behind the transparent proxy.
In other to successfully bypass any transparent proxy from your internet service provider, you have to use a Virtual Private network.
Bypassing transparent proxies using the best VPNs
Now that we have managed to spell out the meaning of transparent proxies, we can now proceed to outline the way it can be bypassed. With the way the transparent proxies work, it relies on the fact that it can be able to access your traffic and be able to redirect your traffic. Logically, the thing that you need is something that blocks out your ISP as well as a transparent proxy from being able to access your traffic.
This is where the VPN is purposeful. The VPN typically works in two ways: The VPN is typically created to have all your data encrypted. Also, it works to redirect your entire traffic by channeling this to pass through a secured server.
This encryption of data shields you from having your data stolen; however, the traffic rerouting provides the highest level of data protection available. Simply, each time that a user makes of the VPN they are connected to the server being made available by the VPN. Which implies that the user now uses the particular server of the VPN to move their traffic about rather than the servers provided by their ISPs? Conversely, the VPN will prevent your traffic from reaching the server of the ISPs. As a result, the transparent proxy will not be effective.
The best VPN also masks your IP Address
Typically, the ISP that you use will not be able to see that you are making use of the VPN because, at this point, they are unable to monitor your traffic. Furthermore, they won’t be able to track or monitor your online activities.
Because the server you are using is not from your ISP, the VPN typically will also mask up the IP address of your connection. Rather than indicating your true IP (that is typically given by the ISP you use), you will now be assigned the IP address that comes from the position of your assigned server.